An online community is a community that forms on the internet. An online community is a group of people interacting, sharing, and working toward a common goal and members interact via social networks, such as Twitter, Facebook, and Google+. They also share in forums, e-mail groups, and even in the comments sections of blog posts and news articles. An online community can also expand out into online community games like Call of Duty or Paradise Cove. Social Media Today have a very informative article on what an online community is. Its described as many things and Elliot Volkman, co-founder and writer for Social Media Today gives a very technical description online communities. He breaks it down into roles and how people participate in online community functions. I suppose from reading the article I used to be a free member on Paradise Cove and I swiftly moved to an active lurker the a contributor and eventually a paid member!
As a longstanding member of Paradise Cove, I talk to people about the same things I would in real life and as I would on Facebook, Twitter or Instagram but its more around a specific topic, product, to offer tips, or sometimes I act as a mentor for newer players. I believe people join online communities because people at home in the offline world don’t share similar passions. So they come online to talk at length with people similar to them who “get it.”
Some people see online communities as seedy internet forums. However they are no longer primitive or explicit forums where hobbyists discuss their crafts or strange interests. Marketing teams now target online communities on Facebook, YouTube and even the game I play, Paradise Cove. Online communities are ideal for word-of-mouth marketing campaigns and we frequently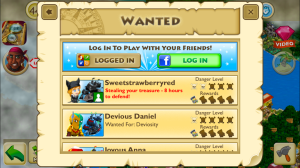 discuss products and you feel the feedback and reviews you get from your friends on the online community are valid… and of course after you buy or try it… you still have to come back and continue playing online with these people. You can connect with Facebook friends on Paradise Cove also.
discuss products and you feel the feedback and reviews you get from your friends on the online community are valid… and of course after you buy or try it… you still have to come back and continue playing online with these people. You can connect with Facebook friends on Paradise Cove also.
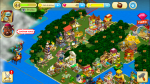
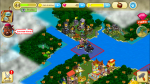
The game Paradise cove has been available on the iTunes store since 2012 and I started playing the game then. The objective of the game is to design, construct, upgrade and enhance the Island. For fast development in the game, you really are required to buy ‘rubies’ to upgrade your ships and pass special quests. It has taken me until this year to get to level I am on, without bowing to the pressure of buying rubies and I am now on lv 44.
The pressure to buy started in February 2015 when I had not played on Paradise Cove for about a month. I returned to my island to find that ‘Sweetstrawberryred’, ‘Gamer189’, ‘Dndos12’ etc had 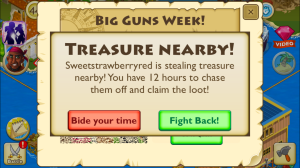 attacked my cove, looted the land, and scuttled my ships. I was devastated. It sparked an anger in me that led me to enter in my iTunes password and I bought a sack of rubies worth 10.99 in real money. It meant in my online community that I could instantly repair my ships, complete a few ‘special quests’, and get this, BUILD back up on my LEVELS. I was heartbroken.
attacked my cove, looted the land, and scuttled my ships. I was devastated. It sparked an anger in me that led me to enter in my iTunes password and I bought a sack of rubies worth 10.99 in real money. It meant in my online community that I could instantly repair my ships, complete a few ‘special quests’, and get this, BUILD back up on my LEVELS. I was heartbroken.
The hardest thing by far to stop doing, was paying for rubies & they constantly have these ruby sales which gets you easily addicted!!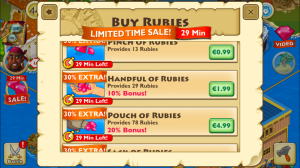 I progressed so far in my group challenges with my paradise cove friends, an I enjoyed the rush of being leagues ahead. I was bumped down to level 37 while I had a month solstice from the game. Without buying rubies or items for quests, It would have taken me a few months to level back up. I leveled back up to lv 44 in a week.
I progressed so far in my group challenges with my paradise cove friends, an I enjoyed the rush of being leagues ahead. I was bumped down to level 37 while I had a month solstice from the game. Without buying rubies or items for quests, It would have taken me a few months to level back up. I leveled back up to lv 44 in a week.
The second hardest thing for me after my month away to work back, was the respect of my craft guild buddies and my quest friends along with my Island allies. I posted a post on one of my guild pages and asked a question about one of our tasks, and no one replied to me. I felt it was because of my level and my lack of contribution. I found myself writing an apology post to my Paradise Cove community buddies for being offline so much.
Screen Shots of my Island on Paradise Cove
Overall, as much as I complained about the cost of the game, I do believe when you are in full swing, playing the game, that there is great engagement and team work involved. I really enjoy playing Paradise CoveYouTuber Rosianna Halse Rojas, gave a TED talk in Brighton about engagement and involvement on online communities and her argument though the course of the TED talk, is that while the internet is seen as a distraction, it also gives a chance for people who would be quite introverted or even how certain people who would have just different interests can engage in an online environment and communicate through the online community or game.








 Phone hacking to me feels more invasive. With
Phone hacking to me feels more invasive. With 






 ly selfie accessory to date that I was aware of was the selfie stick, but there’s more. They have composed a list of the
ly selfie accessory to date that I was aware of was the selfie stick, but there’s more. They have composed a list of the  ts as a photographer. It’s almost like the amature’s progression button towards professional techniques. HISY aims to help you take a selfie with an iPhone more easily. It’s a simple button that connects to the phone via low-energy Bluetooth, and takes control of the built-in shutter camera. HISY’s battery lasts for two years if you take 100 photos daily, which means the little’o button will last for a while. And when it expires, you can replace it with a plain CR2032 cell straight out of your local electronics shop. Of course, the gizmo can be used not just for selfies, but for all kinds of photographs too, even video. HISY doesn’t need a special app to run, it connects directly to the iPhone’s camera app, and can only be used with iPhones ISO7 or newer. Unlucky for the Android selfieists.
ts as a photographer. It’s almost like the amature’s progression button towards professional techniques. HISY aims to help you take a selfie with an iPhone more easily. It’s a simple button that connects to the phone via low-energy Bluetooth, and takes control of the built-in shutter camera. HISY’s battery lasts for two years if you take 100 photos daily, which means the little’o button will last for a while. And when it expires, you can replace it with a plain CR2032 cell straight out of your local electronics shop. Of course, the gizmo can be used not just for selfies, but for all kinds of photographs too, even video. HISY doesn’t need a special app to run, it connects directly to the iPhone’s camera app, and can only be used with iPhones ISO7 or newer. Unlucky for the Android selfieists.



















![keep-calm-and-keep-your-password-secret[1]](https://aoifenimhurchucybercultures.files.wordpress.com/2015/03/keep-calm-and-keep-your-password-secret1.png?w=257&h=300)





 Y
Y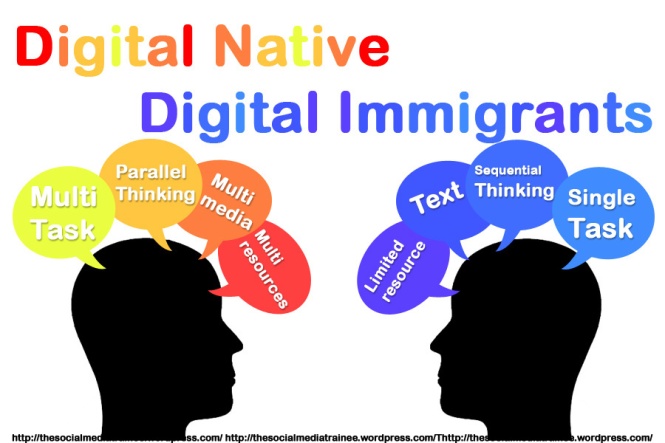



 Cybercultures is becoming a very talk about topic today. Cybercultures is a culture about the new or emerging developments from the use of computer networks for communication, entertainment and business.
Cybercultures is becoming a very talk about topic today. Cybercultures is a culture about the new or emerging developments from the use of computer networks for communication, entertainment and business.
