The importance of Online Media Tactics for Effective Political PR campaigns that will Influence Voters between the ages of 18-25
Introduction
Political Public Relations communicators need to create awareness of the party and its policies and manage the relationships and the messages that they want their parties to convey. For general elections and referendums in Ireland, TD’s and political parties predominantly use traditional means of political communications and their public relations and is generally carried out by face to face house campaigning. They also use leaflets that they put in post boxes and fix posters on poles around the country. Professional communicators need to realise that publics are not that interested in the political parties themselves but instead the message that they share. It is important that we realise that the public needs to have a visual and informative image of the political party and of their policy issues which help to influence the mind of the voter.
The target age bracket that will be focused on throughout the course of this report will be from 18-25. 120,000 voters in this age category are not registered in Ireland to vote and for the up coming referendum on same-sex marriage in May. It is that demo graph of people who are most likely to vote yes. September 2014, a Red C poll, commissioned by the NYCI, found that up to 30pc of 18-25 year olds were not listed on the electoral register. (Youth.ie, RED C Poll, 2014). RED C is the most frequently published and respected political pollster in Ireland. They publish political tracking polls for our key client The Sunday Business Post on a monthly basis, as well as conducting polls for other media sources, betting groups, political parties and candidates. (RED C Research, 2014)
With the frequency of people turning 18 in Ireland since, that statistic has a very probable possibility of being higher. This is a distinct age bracket where political parties can target effectively through use of online media along with the traditional PR tactics they currently use.
Statistics from (Digital Training Institute, 2014) show that 62% of the population aged 15 years and above are members of Facebook and just over two-thirds of these account holders use Facebook daily. With the shift to social media and online use, our political parties are falling well behind the times in terms of campaigning for support, engaging with their publics and delivering their messages. (The Journal, 2014)
Through research both primary and secondary, I have complied a summary of recommendations to show how political parties can effectively target this age bracket by using traditional & new media PR tactics.
-
 A revamp of the current style of face to face canvassing to target 18-25 year olds is mandatory to re-engage with this lost target age bracket. Canvassing online can help improve the communications of a political candidates message if canvasing is provided online. 18-25 year olds are not interested in face to face canvassing and it really only works for older voters.
A revamp of the current style of face to face canvassing to target 18-25 year olds is mandatory to re-engage with this lost target age bracket. Canvassing online can help improve the communications of a political candidates message if canvasing is provided online. 18-25 year olds are not interested in face to face canvassing and it really only works for older voters. -
By using targeted marketing on social media networks, Professional Communicators can effectively pursue un registered voters and explain to them why it is important to vote. If PR communicators fail to see this gap in their current style of communications, the figure of 120,000 unregistered voters will increase. (Personal Communication, Irish Political Communications Survey, 2015).
-
Timing and scheduling online messages out on social media applications at high usage times will help disperse messages from professional communicators. Using applications like Hoot-suite will aid in this delivery as all the different social media platforms have different times and scales of usage (Digital Irish Consumer Report).
-
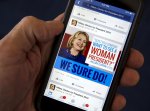 Taking inspiration from UK and American political PR campaigns like Clinton’s digital campaign will show how effective that broadcast can be when targeting 18-25 year olds. Imparting a speech on Youtube, declaring the launch of her campaign of Twitter and her usage of Facebook, created a Media Blitz. YouTube videos can be shared freely on Facebook, Twitter, Google and other networks, and posted to blogs or websites. This might grow organic views to a level where paid ad placement isn’t needed. By harnessing your supporters, and encouraging them to share your video online, you have the ability to reach your electorate directly in their homes and on their mobile devices.
Taking inspiration from UK and American political PR campaigns like Clinton’s digital campaign will show how effective that broadcast can be when targeting 18-25 year olds. Imparting a speech on Youtube, declaring the launch of her campaign of Twitter and her usage of Facebook, created a Media Blitz. YouTube videos can be shared freely on Facebook, Twitter, Google and other networks, and posted to blogs or websites. This might grow organic views to a level where paid ad placement isn’t needed. By harnessing your supporters, and encouraging them to share your video online, you have the ability to reach your electorate directly in their homes and on their mobile devices. -
Youtube is also another online social media application that to date is unused by professional communicators. YouTube tutorials are increasingly popular, with 31% saying they view regularly. An issue was highlighted in the Personal Communications survey 2015 by comments left by participants. Some found it very difficult to register to vote as there was no accurate guide to follow & there was no way to apply online. Another recommendation I would have for PR communicators would be to create an online medium for people to be able to vote and to share it by targeted marketing through social media. The ease of access would greatly increase the amount of registered voters in Ireland. These new digital PR communication techniques were used recently by Hillary Clinton.
 In April 2015 she launched her political PR campaign via Social media. There was no press conference or media gathering and it was announced by one tweet and a Youtube video. The massive social media blitz sparked a huge response for Clinton and set her campaign off to a great start. The Americans have realized that social media has quickly become one of the most prominent ways for politicians to connect and engage with the public. Clinton and other candidates are now going beyond the ‘traditional’ channels of Facebook and Twitter, to others, such as Snapchat and Periscope, as they seek for broader ways to engage with voters. (The Journal, 2015)
In April 2015 she launched her political PR campaign via Social media. There was no press conference or media gathering and it was announced by one tweet and a Youtube video. The massive social media blitz sparked a huge response for Clinton and set her campaign off to a great start. The Americans have realized that social media has quickly become one of the most prominent ways for politicians to connect and engage with the public. Clinton and other candidates are now going beyond the ‘traditional’ channels of Facebook and Twitter, to others, such as Snapchat and Periscope, as they seek for broader ways to engage with voters. (The Journal, 2015) -
 Measurement of the effectiveness of a Political PR campaign can be measured more effectively online. While there is no effective way of measuring the ROI of a poster campaign, there is with video – YouTube campaigns can also be tweaked within minutes ensuring you get the most out of the budget. Imagine being able to change where your poster appears at the click of a button, based off real-time data of how many people are looking at it where it is now. While there’s still a place for traditional forms of advertising, video commercials will be more effective in terms of being eco-friendly, cost efficient and in targeting a candidate’s electorate.
Measurement of the effectiveness of a Political PR campaign can be measured more effectively online. While there is no effective way of measuring the ROI of a poster campaign, there is with video – YouTube campaigns can also be tweaked within minutes ensuring you get the most out of the budget. Imagine being able to change where your poster appears at the click of a button, based off real-time data of how many people are looking at it where it is now. While there’s still a place for traditional forms of advertising, video commercials will be more effective in terms of being eco-friendly, cost efficient and in targeting a candidate’s electorate.![socialmedia.org[2]](https://aoifenimhurchucybercultures.files.wordpress.com/2015/05/socialmedia-org2.png?w=300&h=255) Professional communicators can show results by adapting to online methods as they can gauge their measurement. Youtube videos will show how many views and also leave spaces for comments, which provides a facility where members of the public can respond back with comments. Video ads can be distributed through specific filters allowing refined audience targeting and video will attract 3 times more inbound links than posts with plain text. (Viddyad, 2014). Its important to deliver a message and give people the opportunity to communicate back. The public information model from Grunig and Hunts 4 models of communications, is currently the preferred method of communication for Political communicators. PR practitioners need to adjust to the two way symmetrical model and use two – way communication styles. This will enable professional political communicators to negotiate with publics, resolve conflict and promote mutual understanding and respect between the political party, member, representative or message to its publics. There is a high level of activism on social media and its users like to contribute. Grunig & Hunt, 1984).
Professional communicators can show results by adapting to online methods as they can gauge their measurement. Youtube videos will show how many views and also leave spaces for comments, which provides a facility where members of the public can respond back with comments. Video ads can be distributed through specific filters allowing refined audience targeting and video will attract 3 times more inbound links than posts with plain text. (Viddyad, 2014). Its important to deliver a message and give people the opportunity to communicate back. The public information model from Grunig and Hunts 4 models of communications, is currently the preferred method of communication for Political communicators. PR practitioners need to adjust to the two way symmetrical model and use two – way communication styles. This will enable professional political communicators to negotiate with publics, resolve conflict and promote mutual understanding and respect between the political party, member, representative or message to its publics. There is a high level of activism on social media and its users like to contribute. Grunig & Hunt, 1984).
Reference Section
Primary Research:
Online Survey 2015
-
Personal Communication, Irish Political Communications Survey, 2015, Results on request.
Secondary Research:
- RED C Poll on Youth.ie: http://www.youth.ie/nyci/RedCNYCI-poll-30-young-people-aged-18-25-not-registered-vote
- Digital Training Institute: http://www.digitaltraininginstitute.ie/social-media-trends-in-ireland-may-2014/
- Red C Research: http://www.redcresearch.ie/polling#sthash.8WMjaVsz.dpuf
- Video Blog: http://blog.viddyad.com/2014/04/28/case-study-irish-political-marketing/
Books Referenced:
-
Ronald D Smith, 2013.Strategic Planning fro Public Relations. Routledge.
-
Ellen Grunig, 2003. Public Relations a Practical Approach. Gil & Macmillan
Reports Referenced:
-
Shane O Leary, Irish Digital Consumer Report 2014










 Phone hacking to me feels more invasive. With
Phone hacking to me feels more invasive. With 

















![keep-calm-and-keep-your-password-secret[1]](https://aoifenimhurchucybercultures.files.wordpress.com/2015/03/keep-calm-and-keep-your-password-secret1.png?w=257&h=300)

